Full Transaction Observability
Modern web applications typically don’t run in a vacuum. It’s common for a web service to need to access other services, such as an SQL database, in the course of its activities. There are two ways that this backing services can be handled when running ReGrade: 1) Runtime comparison of backend interactions and 2) mocking or creating fake instances
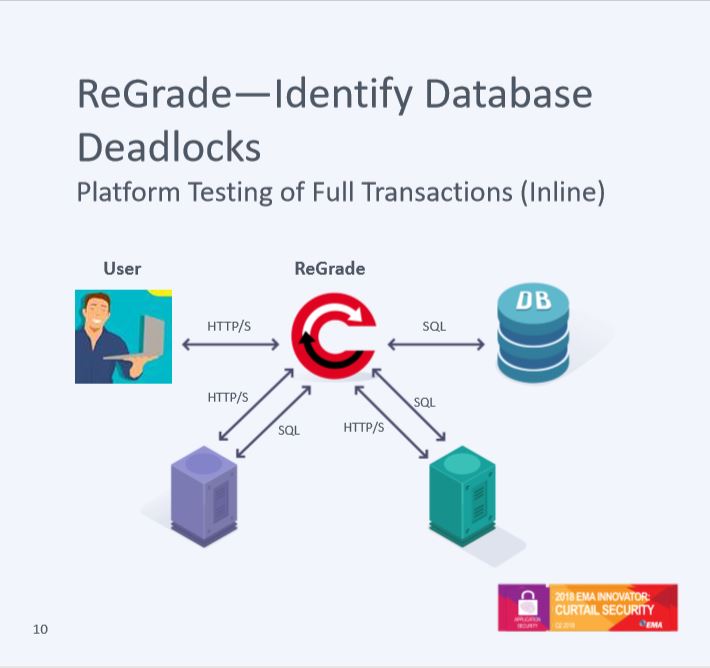
1) Runtime comparison of backend interactions is a powerful approach. The backing services do not need to be duplicated or modified in any way. When each tested version of the web service makes a request to the backing service it is directed first to ReGrade. ReGrade compares the queries that are being sent by each service to determine if their interactions with the backing service have changed. Depending on user’s preference, ReGrade will either send only queries that are sent by all of the services, or will send the queries sent by the production service. When the services have all sent the same query, they can also all receive the same reply. This allows ReGrade to execute the query on the backing service exactly one time and then provide the result to each of the web services being tested. This avoids problems with duplicate transactions that otherwise might occur, while also providing more detailed insight into exactly where the interactions with the backing service were different.
2) Mocking, creating a fake or duplicate instance of the backing service, has been a typical and limited approach. Each compared instance of the web service communicates with its own separate set of backing services. At a designated cut-off point the states of the backing services are compared to see if they have been kept properly synchronized by the web service being tested. For example, if the backing service is an SQL database then at the end of the test run the two database copies can be compared to see if there are any discrepancies. This requires the capacity to duplicate or modify the backing resources and ultimately shows only that a difference happened as a result of the test run. Comparing the state after the test completes does not show exactly where a difference occurred in the interactions with the service. With mocking, ReGrade supports testing applciations with backend databases, or other backend services and APIs.
